Companies go to great lengths to protect sensitive personal and financial information. But as cybercriminals become increasingly sophisticated, scams are on the rise, putting key information at risk of being compromised.
Scammers often use phishing techniques to access secure data or personal information. Cybersecurity company Egress reports that QR Code scams in emails accounted for 12.4% of all phishing emails in 2023, jumping from 1.4% just a year prior.
Health care, hospitality, education, and insurance industries are most likely to be targeted with phishing schemes, according to a 2024 report from cybersecurity firm KnowBe4.
While companies have long been aware of email phishing scams, QR Code “quishing” scams have presented a new way to manipulate and deceive. Quishing targets businesses in a few ways: Instead of taking users to legitimate websites, QR Codes direct users to fake websites that may prompt them to provide banking access or enter personal information like passwords. Fake QR Codes can also prompt users to download malware onto their devices, which can wreak havoc.
Phishing is one of the most common crimes, according to the Federal Bureau of Investigation’s Internet Crime Complaint Center. Phishing crimes were reported nearly 299,000 times in 2023—a 161% increase since 2019, according to a 2023 report from the Bureau. Some of those scams include the ubiquitous black-and-white squares that people have hijacked in phishing scams, prompting the Federal Trade Commission to issue a warning about the risks of QR Codes in 2023.
Savvy workers might assume they’re not susceptible to scams, but those geometric codes, difficult to distinguish from one another, may appear more benign than a sketchy URL.
“They want you to scan the QR Code and open the URL without thinking about it,” Alvaro Puig, a consumer education specialist for the FTC, said in a statement.
Quishing scams often leverage brand names or familiar emails to dupe busy employees. A common scam is phishing emails that impersonate Docusign. Bad actors ask people to access funds from a “funds settlement agreement” by scanning a QR Code, which points them to a fake Docusign website where they can fork over their sign-in credentials.
Other common Quishing attempts include Zoom meeting invitations and HR reminders for policy reviews, according to KnowBe4. The company’s research found that globally, nearly 49% of clicks on phishing links in the third quarter of 2024 purported to be emails about HR or IT matters.
Consumers may be familiar with public-facing scams, such as fraudsters tricking people into sharing payment information on fraudulent websites using fake QR Codes stickered onto parking meters. Fraud investigations into fake QR Codes have been underway across the nation, in cities like Austin, Houston, and San Antonio in Texas, as well as Newtown, Massachusetts, for instance.
Meanwhile, however, businesses may face a different kind of threat from within if employees aren’t aware of the risks of QR Codes or if hackers infiltrate systems to access information protected by QR Codes that lack extra security. To minimize such risks, organizations are increasingly adopting structured cyber incident response strategies to prepare for, detect, and effectively respond to potential breaches.
As workplaces grapple with new security threats, businesses may seek extra protective measures. Uniqode examined industry reports and news coverage to find out how new technologies like encrypted QR Codes and ink authentication can help protect workplaces from scams.
How encrypted QR Codes work
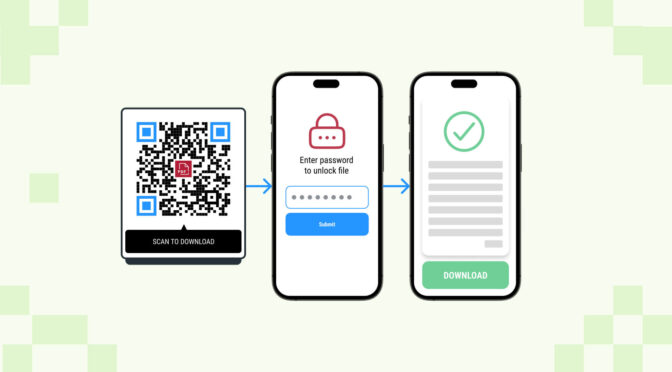
Companies can protect themselves by using encrypted QR Codes to secure their links further. There are varying levels of encryption, but they generally utilize a secret decryption key that allows the scanner, typically a phone, to read the QR Code before moving forward.
For example, Google experimented in 2012 with encrypted QR Codes that allowed people to log into their email from a public computer. Users could scan the QR Code on their smartphone with the approved credentials; once this decryption passed, the email on the public computer would automatically log in.
QR Codes can also be password protected, requiring a code to open the link and proceed. Dynamic QR Codes allow users to add passwords that can be changed later, whereas static QR Codes, once created, stay the same. Encrypted QR Codes can be helpful in settings where the shared information requires confidentiality or added security, such as health care records, event tickets, and legal documentation.
Encryption helps protect the data stored inside a QR Code so only authorized users can access it. Businesses can use encrypted information to protect confidential consumer information during a breach and as an extra safeguard against extortion. An extra layer of security to guard data from bad actors can also give companies greater peace of mind.
Upcoming tech advances will keep boosting QR Code security
Massachusetts Institute of Technology researchers pioneered Invisible ink authentication, an advanced security measure designed to hide QR Codes in plain sight, such as on documents, to prevent counterfeiting.
Invisible QR Codes have fluorescence – so they cannot be seen by the naked eye or detected by a camera lens. Only users aware of the fluorescence can utilize a specialized filter to detect and scan the code, accessing key information securely.
Another advancement is algorithm-driven anti-copy technology, which adds a layer of security to QR Codes by preventing counterfeiters from passing off knock-offs as the real thing. Unlike regular QR Codes, which can be copied or modified to point users to a fake website, anti-copy security QR Codes have a subtle watermark and use an algorithm for authentication that makes them extremely hard to fake. They’re particularly useful when used in pairs for shipping a product, where the top QR Code can be used multiple times along the shipping route, but the bottom QR Code can only be used once – authenticating the product.
Old-school, street-smart techniques should not be underestimated in their capacity to protect people from quishing scams.
“The good news is that the way to [be] safe from this malicious activity is to use the steps we have already learned from phishing and other social engineering attacks, such as only scanning codes from trusted sources, verifying links are legitimate and looking out for other red flags,” Garrett McManaway, chief information security officer of Wayne State University, wrote in a blog post.
Duke University security guidelines recommend only using native QR Code scanners, checking the URL to see if the code sends the user to the anticipated website, and other website details that signal authenticity, such as a matching logo and color scheme.
Another hallmark of a quishing scam is a false sense of urgency – attempts to push victims to act quickly without thinking, such as contacting someone immediately to deliver a package or log in to an account due to alleged suspicious activity.
People can protect themselves by being wary. Take a moment to think before scanning, avoid short URLs, and if it seems fishy, there’s a good chance it is phishy.
Story editing by Alizah Salario. Additional editing by Elisa Huang. Copy editing by Kristen Wegrzyn. Photo selection by Lacy Kerrick.